Advanced Guide for Roles and Policies
Users and Teams
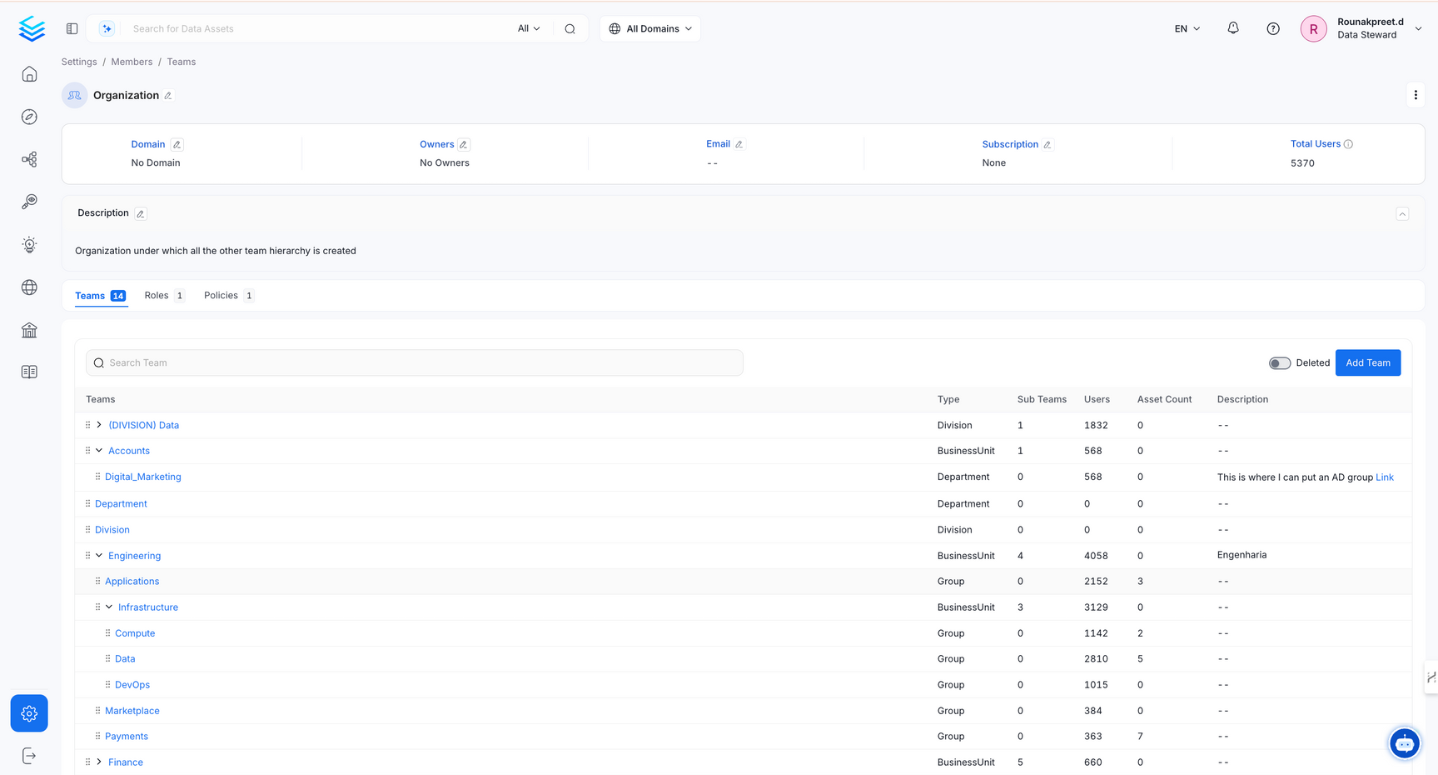
Collate introduces a versatile hierarchical team structure that aligns with your organization’s setup. Administrators can mirror their organizational hierarchy by creating various team types. Organization serves as the foundation of the team hierarchy representing the entire company. Under Organization, you can add Business Units, Divisions, Departments, Groups, and Users. For instance, if your company is Facebook, then the Organization represents entire Facebook itself, which further houses diverse teams like Engineering, Sales, Finance, and Marketing.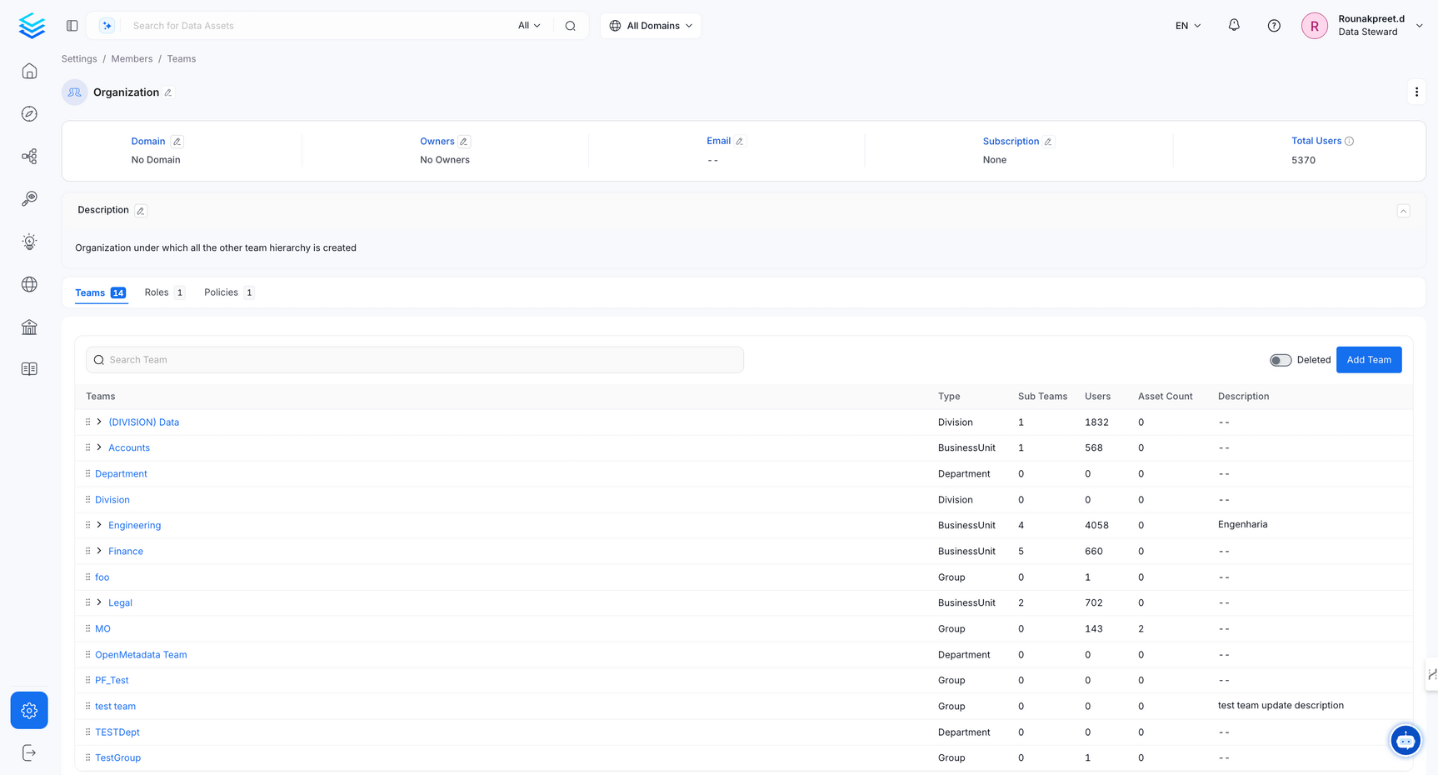
Access Control Design: Roles and Policies
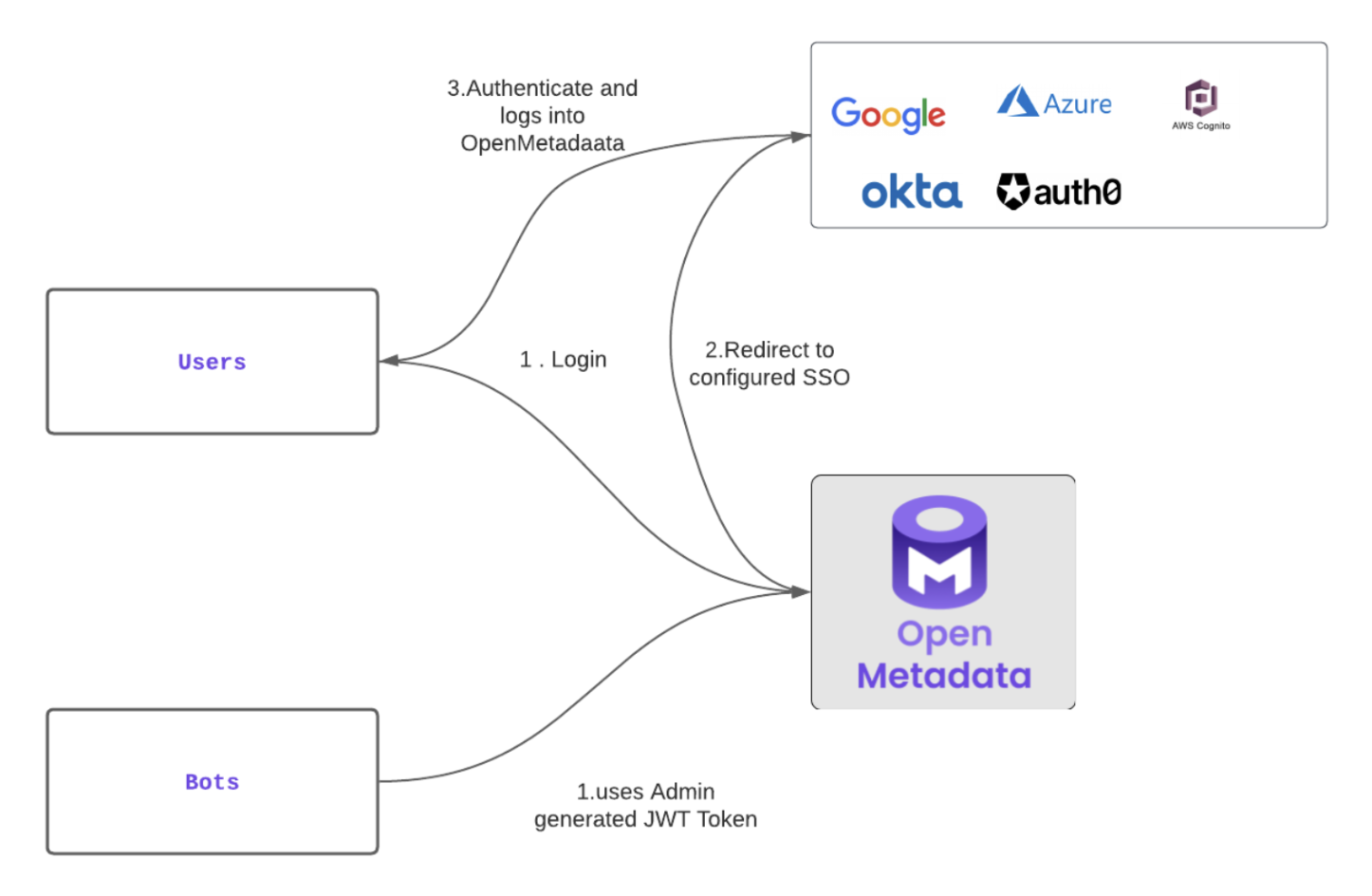
Authentication Flow
Authorization Framework
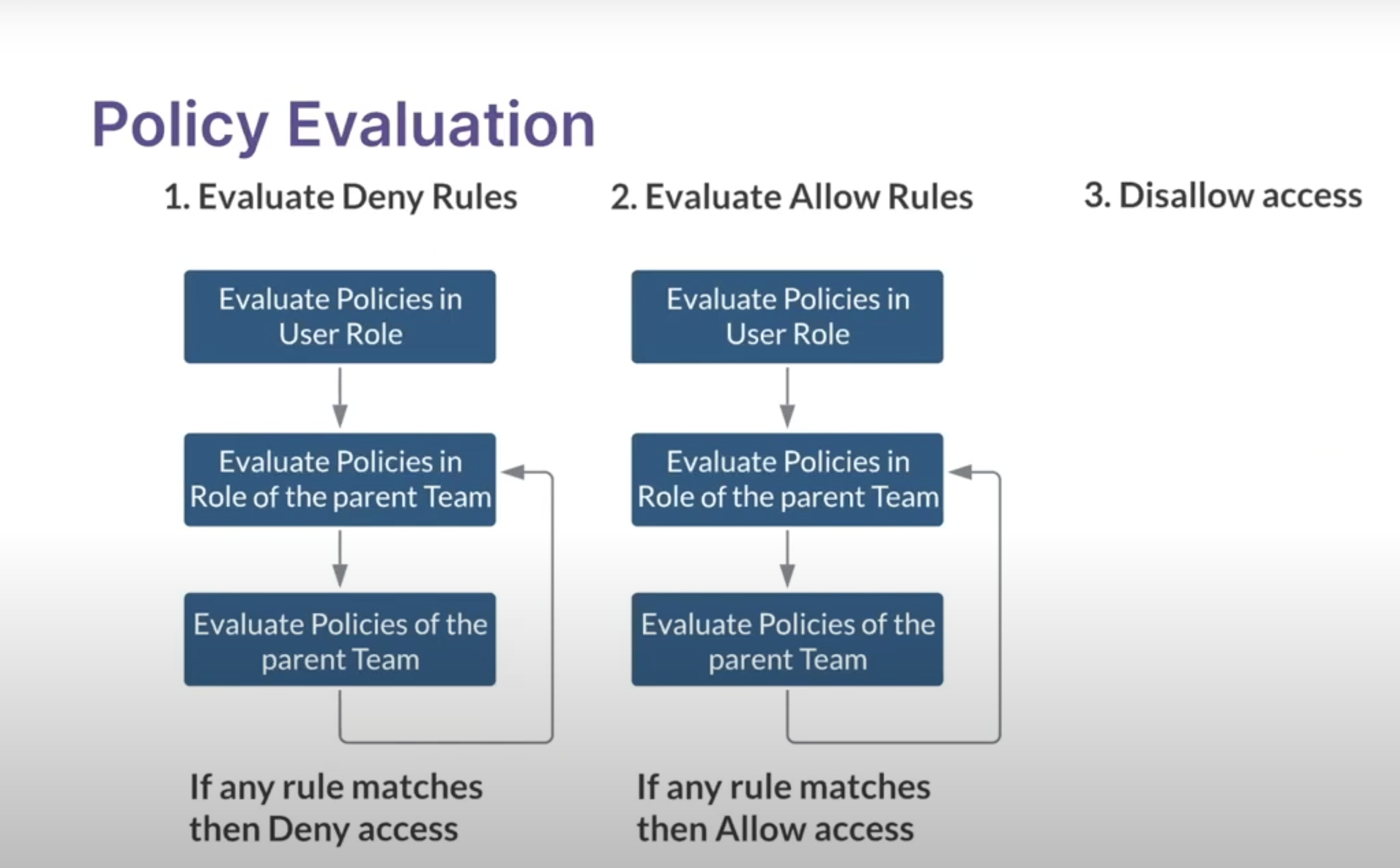
Collate’s authorization is a result of evaluating three crucial factors: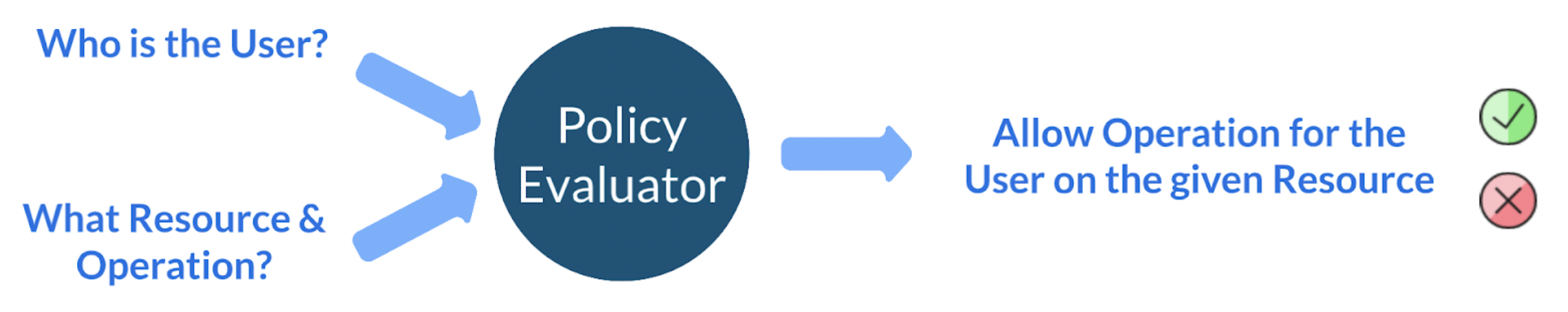
Difference Between ViewBasic and ViewAll in Collate
The operations ViewBasic and ViewAll in Collate differ in the level of detail they provide access to. Below is a detailed explanation of each operation:ViewBasic
- Provides access to the basic details of an asset.
- Includes information such as:
- Description
- Tags
- Owner
- Fundamental metadata
- Excludes more detailed information, including:
- Profile data
- Sample data
- Data profile
- Tests
- Queries
Key Points:
- Suitable for viewing foundational asset metadata.
- Limited access for users who do not require in-depth technical details.
ViewAll
- Provides access to all details of an asset.
- Includes everything available in ViewBasic, along with:
- Profile data
- Sample data
- Data profile
- Tests
- Queries
Key Points:
- Designed for users who need a complete view of the asset.
- Offers comprehensive insights and detailed metadata.
Summary Table
| Feature | ViewBasic | ViewAll |
|---|---|---|
| Basic Details | ✅ Included | ✅ Included |
| Profile Data | ❌ Not Included | ✅ Included |
| Sample Data | ❌ Not Included | ✅ Included |
| Data Profile | ❌ Not Included | ✅ Included |
| Tests & Queries | ❌ Not Included | ✅ Included |
Overview:
- ViewBasic: Focused on essential metadata.
- ViewAll: Provides a complete view, including advanced details.

Building Blocks of Authorization: Rules, Policies, and Roles
Learn all the details of Rules, Policies, and Roles
Use Cases: Creating Roles & Policies in Collate
Tailor you policies to meet your organizational and team needs.